. : Information Security
Information Security is about protecting data and applications from access or tampering by unauthorized parties and malicious elements, both within and external to your business. This requires a two-edged security approach that focuses on reducing the severity and number of vulnerabilities of which diverse threat agents can take advantage of and create impact to one’s business. Regardless of the type of regulation or compliance obligation, the underlying foundation and requirement is to be able to solidly demonstrate sufficient “due diligence” for reducing the probability of a security incident and minimizing the impact.
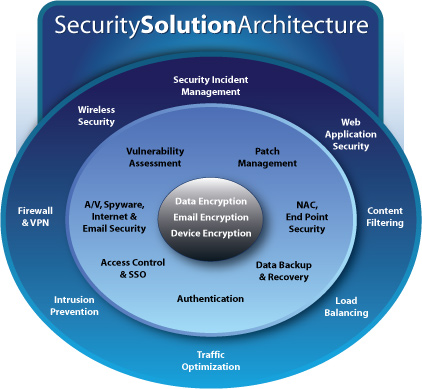
SDI has identified three layers of security protection, as depicted in the diagram above. The three layers are Perimeter Security, Network Security, and Data Security. Part of the risk equation is determining the technical security safeguards, based on agreed upon business impact scenarios, that will offer the optimum return-on-security-investment for reducing vulnerabilities and the corresponding threat prevention. Each layer in the diagram presents the various technical safeguards (solutions) that should or may be needed by companies to protect data, systems and the enterprise.
Secure Datacom combines Best of Breed security solutions and certified professionals to help our clients construct an holistic, layered architecture. We also work with our clients to support this architecture by improving security practice and processes, understanding how to make a policy work, and being able to measure overall security efforts. Rather than staffing a limited size and capabilities team of security professionals, we have partnerships with Security Consulting firms for offering only the A-Team personnel to our clients.
To know more about any of Secure Datacom’s Security Solutions, contact your SDI salesperson or email us.
|